Easy & Quick Guide To Remove Trapget Ransomware
1 min read
Created by cybercriminals, Trapget Ransomware is actually a variant of ransomware namely, NEFILIM, discovered by GrujaRS.
Every malware is created with the bad intention of course. That intention with this malware program is to scare innocent computer users and then extort ransom money from them.
To achieve this aim, ransomware ha
Uninstall TRAPGET Ransomware Automatically
s been designed in a highly sophisticated manner.
Later on, in this blog, we will show how to remove Trapget Ransomware from PC and how to retrieve your locked files back.
However, if in hurry, very quickly you can download FREE SOFTWARE to remove or uninstall Trapget Ransomware from the PC.
>>Free Download Software To Remove Trapget Ransomware Quickly<<
How Trapget Ransomware Extort Ransom Money?
Being programmed with highly advance algorithmic skills, this ransomware intrudes inside the victim’s PC, without their content. Later on here, we will brief you with the methods Trapget Ransomware deploys to penetrate inside the targeted system.
The ransomware once got entered successfully, starts encrypting the victim’s files. It modifies the system’s file names and creates the “TRAPGET-INSTRUCTION.txt” text file… Its basically a ransom note with instructions on how to contact ransomware developers and etc.
Files are modified via appending the “.TARGET” extension to their respective file names.
The generated “TRAPGET-INSTRUCTION.txt” text file, as mentioned above, comprises info on what had actually happened to the system files. Why they are inaccessible and how to make them accessible again.
Target Instruction Generated Note:
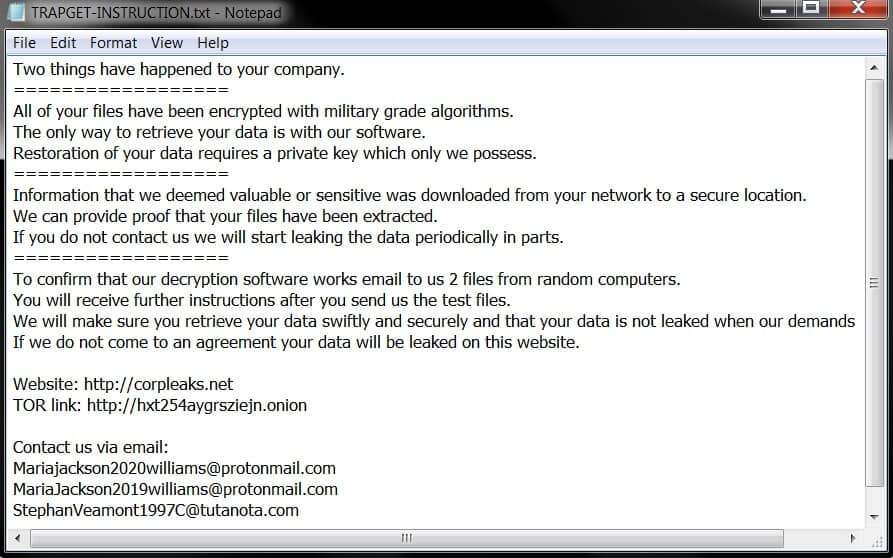


The file tells that ransomware has encrypted files with military-grade algorithms in a manner, that now only way to decrypt them is the usage of software and a private key. Now the twist is that these things one can only purchase from the TRAPGET’s developers.
Victims are required to send two encrypted files for free decryption to mariajackson2020williams@protonmail.com, mariajackson2019williams@protonmail.com, or stephanveamont1997C@tutanota.com email address. And then they are required to wait for further instructions.
In the case of TRAPGET RANSOMWARE, it is clearly stated that victims who will not corporate will be responsible for their website leaking on certain websites.
Now the situation is like you have only one option, i.e., to pay the ransom and get your files back. However, depending on the experiences with several ransomware, it is advised not to make any asked payment, as there is proof that even after payment is done, no decryption key or tool is sent. It’s just a trick to lure innocent PC users into paying their hard-earned money.
So, if have unfortunately encountered issues due to this ransomware, it’s advised never to make any asked payment and instead go for Antimalware Removal Tool.
Though today there is bombarding of antimalware programs in the market, however, we recommend SpyHunter, as it’s the best as per our experience. Later on, will be briefing you on why we recommend that. Nonetheless, if in hurry, you can direct free download it from here…
Now before getting deep into how this software work and how to use it, have a quick glance at how TRAPGET RANSOMWARE intrudes inside the PC.
How Trapget Ransomware Intrudes Inside PC?
Usually, cyber crooks deploy malspam campaigns, malicious email attachments, contaminated external storage devices, and all to perforate TRAPGET Ransomware inside the targeted system. Nonetheless, besides from this, often fake third party software updating tools and unofficial software activation tools are also used by crooks to invade this vicious program inside targeted PC.
Usually, people ask how computer viruses penetrate inside the PC through vicious email attachments.
Well here, allows us to explain how this happens…
So, crooks send emails, having malicious files attached to them to people. Now main intention behind this is to tricks recipients into executing the attached vicious file, which is of course designed to contaminate PC with virus infections. Usually, crooks attach a vicious Microsoft Office Document, archive file (say ZIP, RAR), PDF document, executable file, or Javascript file and wait until the recipient opens it.
Another method, ie., downloading software from unknown or unreliable sources like free file hosting websites, Peer-to-Peer networks (such as torrent clients), freeware download sites, and etc.
OK… so this about how TRPGET Ransomware perforates inside PC.
Now heading onto how to remove or uninstall TRAPGET Ransomware from PC.
How To Remove TRAPGET Ransomware from PC?
If your PC got infected with TRAPGET Ransomware, then my friend you need to remember one thing… As soon as possible, you need to remove this particular ransomware threat from your respective system, as it’s crucial to prevent further file encryption in your system.
Only after uninstallation of this vicious program, you can start your file recovery procedure.
So, here we go…
You can uninstall TRAPGET Ransomware via both Manual Method & Automatic Method.
Note: Manual Method is for those, who are experienced, PC users. Who does have knowledge of PC? Novice PC users can risk their system and data with the implementation of the manual method.
So, better is to go with the Automatic Method to remove TRAPGET Ransomware from PC.
Uninstall TRAPGET Ransomware Automatically
SpyHunter is an antimalware program designed to scan for, identify, remove, and block vicious malware programs from the PC.
Programmed with highly sophisticated algorithms, the software can trace the exact locations of even such vicious programs, which are easily not detected by any antimalware programs.
SpyHunter has been developed and engineered with precision programming, with the sole motto of providing sophisticated online protection and security. The software does offer an easy-to-use interface.
System Requirements:
Version: 5.9.23
File Size: 89.2 MB
File Format: EXE (Standalone) system
Operating Systems Supported



Minimum Hardware Requirements
1 GB RAM or more
1 GHz CPU or faster
200 MB of available Hard Disk Space or More
Instead of providing you with steps on how SpyHunter antimalware program works, we think its more suitable to show you how it works… So,
Watch How SpyHunter Works
Uninstall/Remove TRAPGET Ransomware using Manual Method
- Open up Task Manager
- Make right-click on the ‘Name’ button and then add the ‘Command-Line’
- Find a “Strange Process”, the folder of which probably is not suitable for it.
- Go to the “Process Folder” and then remove all the files
- Move to the Registry and then remove all keys associated with the process
- Now go to the AppData folder and then remove all strange folders, which you can find.
So here we end up about TRAPGET Ransomware removal.
Now, have look at how to restore files encrypted by TRAPGET Ransomware.
How To Decrypt Files Encrypted or Locked by TRAPGET Ransomware?
Regarding the restoration of files encrypted by TRAPGET Ransomware, Stellar Data Recovery Software is the best Windows Data Recovery Software. This software proficiently helps restore files, no matter how hard it had got encrypted.
About Stellar Windows Data Recovery Software
Stellar Windows Data Recovery Software is the most tested and most awarded Windows Data Recovery Program, to recover lost or deleted data from any Windows device.
This Stellar software is compatible with almost all the latest versions of Windows OS.
No matter, data is corrupted due to deletion, drive corruption, missing or deleted partition, the software can retrieve all.
How to Restore Data with Stellar Windows Data Recovery Software
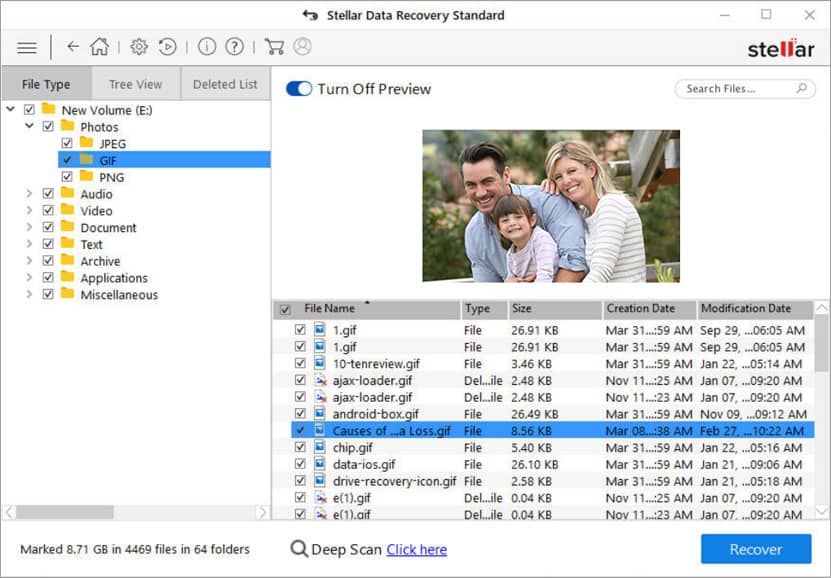
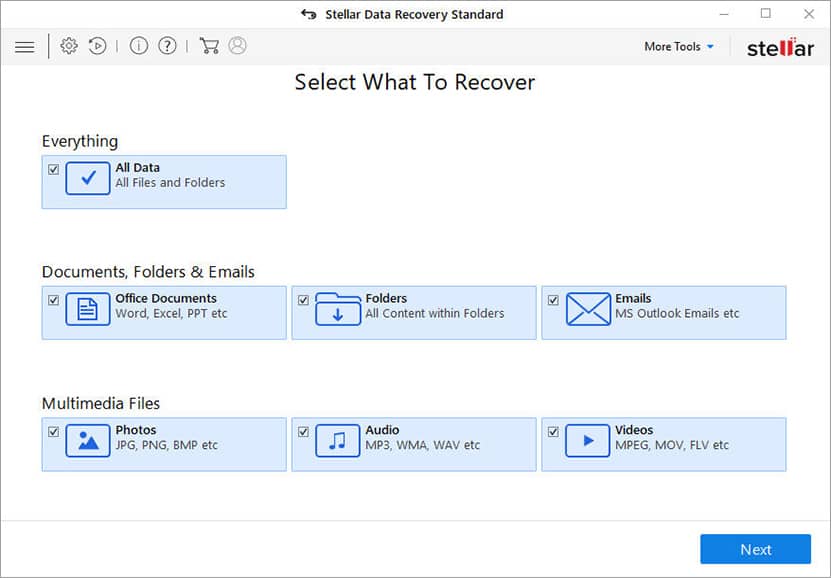
Select File Type: Select the data type you wish to recover and then click Next


Select Recover From: Select the folder location or drive volume and then click ‘Scan’
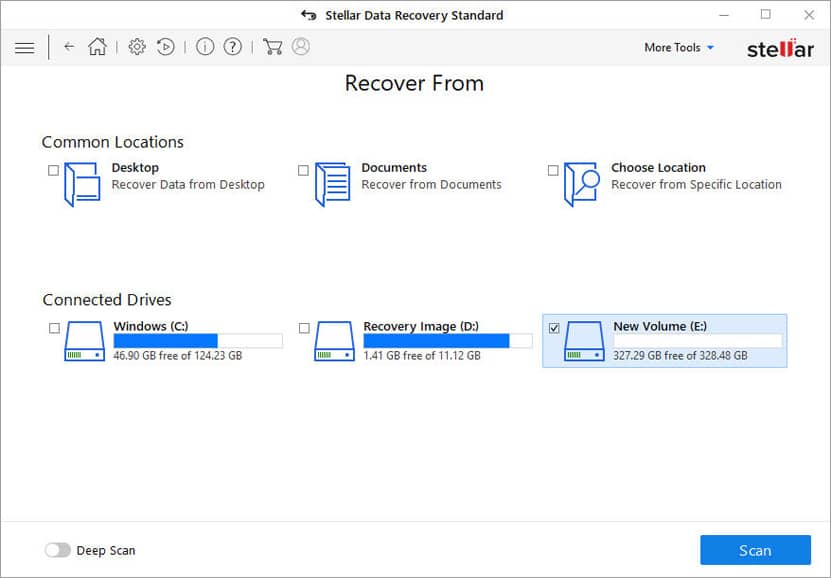


Scan & Recover: Select files after scan and then click Recover to save recovered data.